DNSSEC at the client
Posted by Mark Feldman in Uncategorized on January 31, 2012
 As more TLDs are signed and more ISPs provide validation, a greater focus is being placed on DNSSEC at the client. Client activities include DNSSEC-aware applications, DNSSEC-aware resolution libraries, and validating local resolvers for times when either the ISP doesn’t provide DNSSEC validation or the last mile between the ISP’s resolver and the client can’t be trusted.
As more TLDs are signed and more ISPs provide validation, a greater focus is being placed on DNSSEC at the client. Client activities include DNSSEC-aware applications, DNSSEC-aware resolution libraries, and validating local resolvers for times when either the ISP doesn’t provide DNSSEC validation or the last mile between the ISP’s resolver and the client can’t be trusted.
The Internet Societys’s Deploy360 Programme has recently put up a list of developer libraries and is soliciting additional input from the community on other libraries.
Members of the DNSSEC Deployment Initiative have been using NLnet Labs’ Dnssec-Trigger on Mac and Windows systems to provide local DNSSEC validation.
Comcast knows when your DNSSEC is bad or good…
Posted by Mark Feldman in Uncategorized on January 25, 2012
so be good for goodness sake.
As reported on the DNSSEC-deployment mailing list (subscribe here), Comcast is analyzing the major DNSSEC failures they’re seeing and publishing the results for the benefit of the community.
The first such failure to be analyzed occurred on the 18th, coincident with the web-wide protests against SOPA and PIPA, with NASA.gov. The report (770KB PDF) was published on Comcast’s DNSSEC Information Center.
As an early adopter of DNSSEC, we remain committed to helping other implementers learn from our experiences.
More than just standards
Posted by Mark Feldman in Uncategorized on January 23, 2012
The Internet Society Deploy360 Programme is a new initiative that provides real-world IPv6, DNSSEC, etc. deployment information. Deploy360 aims to bridge the gap between the IETF standards process and final adoption of those standards by the global operations community. Deploy360 creates and promotes resources that are easy to understand and quickly actionable by the very IT professionals responsible for the implementation of new technologies and standards like IPv6 and DNSSEC.
Check out the Internet Society’s Deploy360 Programme and its DNSSEC content.
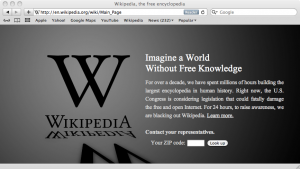
Online protests against SOPA and PIPA
Posted by Mark Feldman in Uncategorized on January 18, 2012
The Internet is on strike. Among the many web sites making their position known, Wikipedia’s English language site is offline (or, hard to get to):
Google has censored their name on their home page and in search results:
All this is in protest to the United States’ proposed Stop Online Piracy and Protect IP Acts. Outside of the battle of free speech versus intellectual property and the potential chilling effects of these bills, the technical enforcement methods in these bills include monkeying with DNS in a way that breaks DNSSEC.
We’ve reported on the issue before, here and here. On Saturday, the White House showed that they understand:
We must avoid creating new cybersecurity risks or disrupting the underlying architecture of the Internet. Proposed laws must not tamper with the technical architecture of the Internet through manipulation of the Domain Name System (DNS), a foundation of Internet security. Our analysis of the DNS filtering provisions in some proposed legislation suggests that they pose a real risk to cybersecurity and yet leave contraband goods and services accessible online. We must avoid legislation that drives users to dangerous, unreliable DNS servers and puts next-generation security policies, such as the deployment of DNSSEC, at risk.
New gTLDs will support DNSSEC from the start
Posted by Mark Feldman in Uncategorized on January 12, 2012
 Today is the first day ICANN is accepting applications for new generic top-level domains (gTLDs). The Applicant Guidebook makes it clear that all new gTLDs must support DNSSEC from the start. While the expansion of the TLD name space has been somewhat controversial, ensuring support for DNSSEC going forward has not been.
Today is the first day ICANN is accepting applications for new generic top-level domains (gTLDs). The Applicant Guidebook makes it clear that all new gTLDs must support DNSSEC from the start. While the expansion of the TLD name space has been somewhat controversial, ensuring support for DNSSEC going forward has not been.
Steve Crocker, chairman of the board of ICANN, said:
The Board and the staff at ICANN have fully understood the importance of DNSSEC. ICANN signed the root in 2010 and has advocated all top level domains be signed. It is only natural that DNSSEC be required from the beginning for all new generic top level domains.
DNSSEC at FOSE 2012
Posted by Mark Feldman in Uncategorized on January 10, 2012
 The DNSSEC Deployment Initiative in conjunction with FOSE will be putting on the workshop, Making DNSSEC the Trust Infrastructure: Where Domain Name Security is Headed, at FOSE 2012 (Washington, DC, April 3-5, 2012).
The DNSSEC Deployment Initiative in conjunction with FOSE will be putting on the workshop, Making DNSSEC the Trust Infrastructure: Where Domain Name Security is Headed, at FOSE 2012 (Washington, DC, April 3-5, 2012).
Registration is now open. The $45 FREE (registration required), 10:00 AM – 4:00 PM workshop on April 3rd, which is aimed at DNSSEC in the US Federal Government, includes these objectives:
- Understand where U.S. Federal DNSSEC deployments stand, and the impact of reductions in Federal data centers and domain names on .gov deployment;
- Learn about new DNSSEC-aware apps that can help speed or ease deployment; and
- Learn where DNSSEC will lead Federal and worldwide Internet security next, in the face of large-scale domain-name attacks and other challenges.
Comcast Completes DNSSEC Deployment
Posted by Mark Feldman in Uncategorized on January 10, 2012
We’ve reached another milestone in the deployment of DNSSEC. Jason Livingood from Comcast writes:
I am pleased to announce that Comcast, the largest ISP in the U.S., is the first large ISP in the North America to have fully implemented Domain Name System Security Extensions (DNSSEC). As part of our ongoing efforts to protect our customers, DNSSEC is now automatically included as part of Comcast Constant Guard™ from Xfinity.
Read more on the Comcast Blog.
A Christmas goat shows uptick in DNSSEC usage
Posted by Denise Graveline in Uncategorized on December 19, 2011
Writing in CircleID, Interlan CTO Torbjörn Eklöv described a novel test of DNSSEC in The Christmas Goat, IPv6 and DNSSEC — Second Season. His company was asked for the second year in a row to assist with load share in the live-streaming of the famous Christmas Goat display in Gävle, Sweden, a task that allowed him to compare IPv6 usage and DNSSEC validation from visitors to the site. Starting on November 27,
we were able find out that both usage of native IPv6 and DNSSEC validation have increased quite a lot this year. The native IPv6 users increased from 0.1% to 0.5% and the DNSSEC validation from 44% to 72%.
The test, and the goat, had an untimely end when the goat burned down on December 2. “But with the experience from the test last year, and this year, I only need few days to get quite an accurate percentage of the use of IPv6 and DNSSEC from the visitors. This year I did a check after two days, last year I checked several times and the result was surprisingly correct after only a few days,” he reports.
Czech mobile operator Vodafone now secured with DNSSEC
Posted by Denise Graveline in Uncategorized on December 12, 2011
Czech voice and data mobile operator Vodafone has announced that it has secured its domain and web services with DNSSEC, making it the first mobile operator in the Czech Republic to do so. The company notes that its customers have two ways to find out whether their connections are secure:
On the www.dnssec.cz site is an automatic test, which displays a green or red icon showing the key users, whether their connection is, respectively, not safe. The second option offers an add-on for Firefox, which can be downloaded for free from www.dnssec-validator.cz. This program allows you to control whether or not the currently visited domain is protected, again displaying an icon key, this time directly in the address bar of your browser window.
Part of the international Vodafone Group, the company serves more than three million customers in the Czech Republic.
Paypal, more ccTLDs deploy DNSSEC
Posted by Denise Graveline in Uncategorized on December 9, 2011
PayPal has announced that all of its owned and operated domain names are now DNSSEC-secured. It joins several country-code top-level domains that have announced their deployment of DNSSEC in recent weeks. Russia’s .su, which is made up of about 90,000 second-level domain names, has been DNSSEC-signed. The Technical Center of Internet says it plans to sign root national domains .РФ and .RU with DNSSEC in 2012. Also DNSSEC-signed are Uganda’s .ug, Myanmar’s .mm, Slovenia’s .si, New Zealand’s .nz and Tawain’s .tw.



Recent Comments