DNSSEC at the Pub
Posted by Mark Feldman in Uncategorized on June 18, 2012
As seen on the DNSSEC Deployment Working Group email list:
Invitation to Informal Gathering of DNSSEC Implementers in Prague 26 June
On behalf of the DNSSEC Deployment Initiative and CZ.NIC, DNSSEC Implementers are invited to attend an informal gathering to discuss and exchange information on their DNSSEC implementation experiences during the ICANN meeting in Prague, Czech Republic. This is a unique opportunity to meet with and talk to key implementers, such as CZ.NIC, Nominet UK, ISC, IIS Sweden, and others. We do ask that in order to participate you should come prepared to say a few words about your experiences. This is a peer-to-peer event for implementers.
Where: Pivovarsky klub
When: Tuesday, 26 June 2012, 6:00 to 8:00 pm
Note that this event is in addition to the other DNSSEC events scheduled during the ICANN meeting. These are:
Monday, 25 June: 4:00-5:30 pm — DNSSEC for Everybody – Roma, Details: http://prague44.icann.org/node/31657
Wednesday, 27 June: 8:30 am to 1:45 pm — DNSSEC Workshop at ICANN Meeting – Congress I, Details: http://prague44.icann.org/node/31749
**Please RSVP to [email protected] no later than Friday, 22 June if you would like to attend.**
Best regards,
Julie Hedlund
On behalf of Ondřej Surý, CZ.NIC and Steve Crocker and Russ Mundy for the DNSSEC Deployment Initiative
New Revision of NIST Special Publication (SP) 800-81 Under Way
Posted by Scott Rose in Technical guides on June 15, 2012
This inaugural post is the first in a series documenting the update of NIST SP 800-81, Secure Domain Name System (DNS) Deployment Guide. The current version (SP 800-81r1) was published in April 2010. Since that date, DNSSEC deployment Internet-wide had matured and advanced to the point where a new revision is justified.
The goal of the new revision of NIST SP 800-81 is to incorporate updates to recommendations based on currently deployment experiences. There have also been recent developments in specification of new cryptographic algorithms for use with DNSSEC (such as Elliptic Curve). The new revision will add discussion on new crypto algorithms as well as update the existing recommendations for DNS and DNSSEC operation.
We are also planning a new section of the document to provide guidance and recommendations for recursive DNS servers and validators. With DNSSEC deployment on the rise, more enterprises (and even ISPs) are configuring DNSSEC validation. Validation is also a planned required control in the upcoming revision of FISMA (NIST SP 800-53r4), so the new sections will be timely.
The plan is to have regular updates on this blog as the draft revision progresses. This is also one of the forums to discuss the revision during the process. As with all NIST Special Publications, there will be a draft document posted with an official comment period; this blog is simply an attempt to solicit input before the initial public draft is released for public comment.
The views presented here are those of the author and do not necessarily represent the views or policies of NIST.
DNSSEC Workshop at ICANN 44
Posted by Mark Feldman in Uncategorized on June 6, 2012
 As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
As with other recent ICANN meetings, there will be a DNSSEC workshop at ICANN 44. The workshop will be held on Wednesday, 27 June 2012 from 08:30 until 13:45 CEST (UTC/GMT +2 hours). Remote participation is available for the meeting.
The agenda for the meeting as it currently stands:
1. Introduction and Presentation: DNSSEC Deployment Around the World: Steve Crocker, Shinkuro
2. DNSSEC activities in Europe
3. ISPs and Validation
4. The realities of running DNSSEC
5. DNSSEC and Enterprise Activities
6. DANE and other DNSSEC applications
7. The Great DNSSEC Panel Quiz
The Legend of DNSSEC
Posted by Mark Feldman in Uncategorized on June 5, 2012
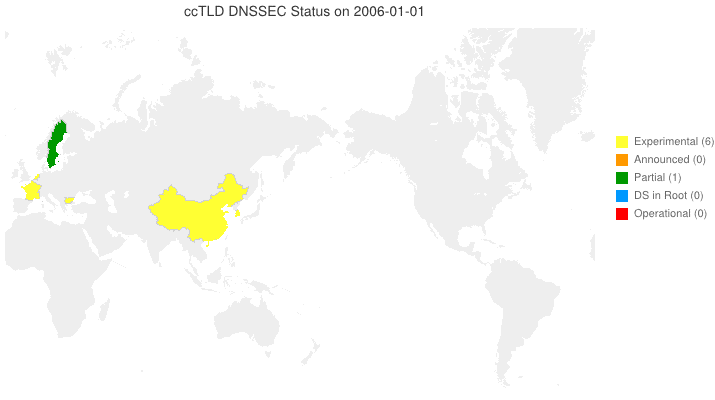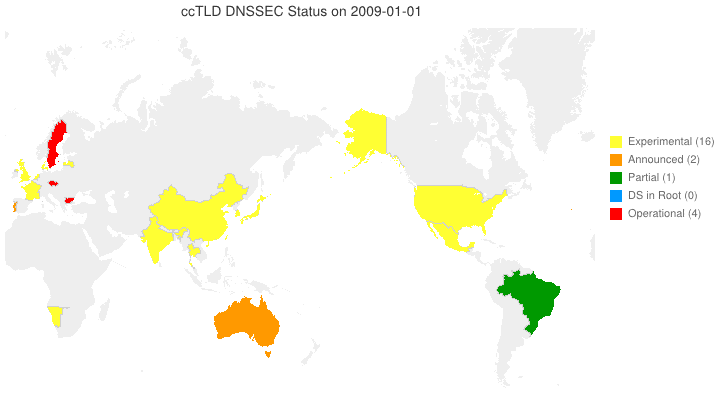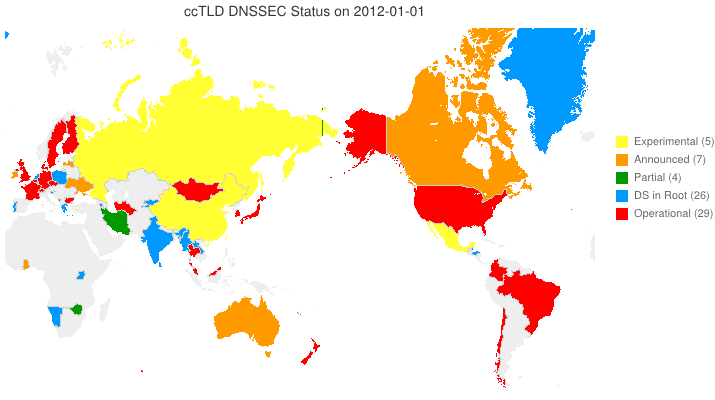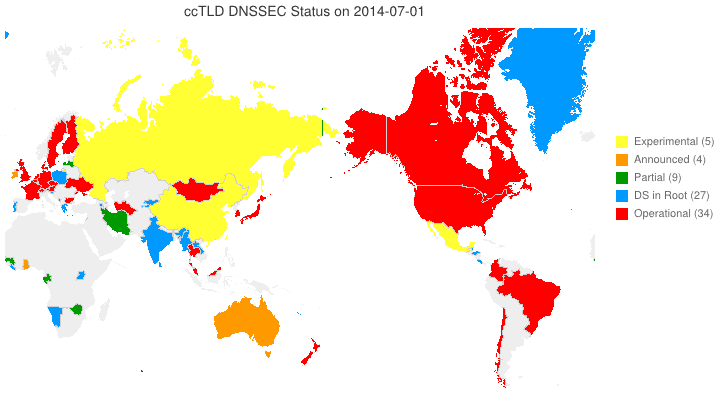
We’ve taken to putting up animated maps of DNSSEC adoption in country code TLDs (ccTLDs) every few months (6 March 2012, 4 June 2012). One question we get is, “So, what does the legend in the maps we produce indicate?” From the past through the date of the map, the following are from observation. For dates beyond the date of the map, the following are either an extension of the observation or based on stated plans.
- Experimental (yellow) — We have reason to believe that the ccTLD is (or will be) experimenting with DNSSEC.
- Announced (orange) — The ccTLD has announced that they will support DNSSEC.
- Partial (green) — The ccTLD has signed their zone, but has not yet passed DS records up to the root and may or may not be accepting signed delegations.
- DS in Root (blue) — The ccTLS is signed and DS records for its KSKs are (or will be) in the root zone, but it is not yet accepting signed delegations.
- Operational (red) — The ccTLD is signed, it has DS records in the root, and it is accepting signed delegations (DS records from child zones).
We can and do identify current Partial and DS in Root statuses programatically. Everything else needs human input. Specifically, your input sent to info @ dnssec-deployment.org.
DNSSEC in ccTLDs, Past, Present, and Future
Posted by Mark Feldman in Uncategorized on June 4, 2012
This animated GIF shows announced, estimated, and actual DNSSEC adoption by ccTLDs from January 2006 through July 2014 as of 4 June 2012. The map is a work in progress. We’re pretty sure about the past and present. If you manage a ccTLD and have a schedule for deployment or have updates/corrections, let us know at info @ dnssec-deployment.org. We’d like to see a more colorful, even completely red, map in the future
SIDN announces DNSSEC operational for .NL
Posted by Mark Feldman in Uncategorized on May 15, 2012
Today, SIDN, the Foundation for Internet Domain Registration in the Netherlands, announced that DNSSEC is operational for the .NL ccTLD (English translation here). The announcement identifies nine registrars offering DNSSEC support for .NL as of today.
“SIDN is committed to making the internet more secure. And we regard DNSSEC as an important tool for achieving enhanced DNS security,” said Roelof Meijer, SIDN’s CEO
DNSSEC makes its debut at NCCDC
Posted by Mark Feldman in Uncategorized on May 10, 2012
Congratulations to the University of Washington, which took first place at the National Collegiate Cyber Defense Competition (NCCDC) in April—the first to emphasize the use of DNSSEC in its challenges.
Each year, the NCCDC tasks teams of collegiate programmers with defending business networks just as in real life, while Red Teams try to penetrate them. This year’s competition involved 126 schools and over 1,500 competitors. Thanks to input from the DHS S&T Directorate, it marked the first time teams were asked to not only sign the zones on their DNS servers, but re-sign them as if they’d migrated their DNS services to a different operating system or application software.
According to organizer Dwayne Williams, roughly 80% of the competitors had heard of DNSSEC before, but less than 10% had ever actually used or implemented it prior to NCCDC. While two of the teams noted that they would like to see simpler, step-by-step instructions for implementing DNSSEC, all of the teams ultimately thought DNSSEC was a technology they planned to look at more in the future.
Overall team reaction was positive and Dwayne Williams notes that the NCCDC succeeded in introducing DNSSEC to all competitors and making them aware of some of its fundamental capabilities.
LISA ’12 Call for Participation
Posted by Mark Feldman in Uncategorized on May 1, 2012
There are still a couple weeks left to submit your DNSSEC papers, etc. to LISA ’12. This, the Usenix Association‘s 26th Large Installation System Administration Conference, will be held December 9-12, 2012 in San Diego, California. General conference information is here.
Crocker inducted into Internet Hall of Fame
Posted by Mark Feldman in Uncategorized on May 1, 2012
Steve Crocker, ICANN board chairmen and DNSSEC Deployment Initiative member, was inducted into the Internet Society’s Internet Hall of Fame as an Internet Pioneer.
Steve was honored for a lifetime of Internet accomplishments, including starting the RFC series. He talked about the RFCs and the openness of Internet protocols several years ago in his New York Times Op Ed, How the Internet Got Its Rules, on the 40th anniversary of the publication of RFC 1.
Steve continues to push for improvement of Internet infrastructure security, including the deployment of DNSSEC and the adoption of BCP 38.
Call for Participation — ICANN DNSSEC Workshop 27 June 2012
Posted by Mark Feldman in Uncategorized on April 26, 2012
As seen on the DNSSEC Deployment Working Group mailing list:
The DNSSEC Deployment Initiative, in cooperation with the ICANN Security and Stability Advisory Committee (SSAC), is planning a DNSSEC Workshop at the ICANN meeting in Prague, Czech Republic on 27 June 2012. The DNSSEC Workshop has been a part of ICANN meetings for several years and has provided a forum for both experienced and new people to meet, present and discuss current and future DNSSEC deployments. For reference, the most recent session was held at the ICANN Costa Rica meeting on 14 March 2012. The presentations and transcripts of the presentations are available at http://costarica43.icann.org/node/29659.
We are seeking presentations on the following topics:
1. DNSSEC activities in Europe
This is a key panel and we are seeking participation from those who have been involved in DNSSEC deployment in Europe as well as those who have a keen interest in the challenges and benefits of deployment. Key questions are to consider include: what would help to promote DNSSEC deployment? What are the challenges you have faced when you deployed DNSSEC? Can DNSSEC make the information users receive more reliable?
2. ISPs and Validation
ISPs are beginning to take the first step to full DNSSEC implementation that will allow web users, with software applications like browsers, to validate that the destination they are trying to reach is authentic and not a spoofed website. We are seeking ISPs to participate in a panel discussion or provide presentations on their DNSSEC deployment plans, challenges, and benefits for users.
3. The realities of running DNSSEC
Now that DNSSEC has become an operational norm for many registries and registrars, what have we learned about how we manage DNSSEC? What’s best practice around key rollovers? How often do you review your disaster recovery procedures? Is there operational familiarity within your customer support teams? Has DNSSEC made DNS more ‘brittle’ or is it just a run-of-the-mill operational practice?
4. DNSSEC and Enterprise Activities
DNSSEC has always been seen as a huge benefit to organizations looking to protect their identity and security on the Web. Large enterprises are an obvious target for DNS hackers and DNSSEC provides an ideal solution to this challenge. This session aims to look at the benefits and challenges of deploying DNSSEC for major enterprises. Topics for discussion:
What is the current status of DNSSEC deployment among enterprises?
What plans do the major enterprises have for their DNSSEC roadmaps?
What are the challenges to deployment for these organizations? Do they foresee raising awareness of DNSSEC with their customers?
5. When unexpected DNSSEC events occur
What have we learned from some of the operational outages that we have seen over the past 18 months? Are there lessons that we can pass on to those just about to implement DNSSEC? How do you manage dissemination of information about the outage? What have you learned about communications planning? Do you have a route to ISPs and registrars? How do you liaise with your CERT community?
6. DNSSEC in the wild
What operational statistics have we gathered about DNSSEC? Is it changing DNS patterns? How are our nameservers handling DNSSEC traffic? Is the volume as expected? Have we seen anything unusual? Are there experiences being documented in the form of best practices, or something similar, for transfer of signed zones?
7. DANE and other DNSSEC applications
Using DNSSEC as a means of authentication for http transactions is an exciting development of DNSSEC. What is the progress of the DNS-Based Authentication of Named Entities (DANE) initiative? (See http://datatracker.ietf.org/wg/dane/.) How soon could DANE become a deployable reality and what will be the impact of such a deployment, e.g. impact on traditional certification authorities (CAs)?
8. The Great DNSSEC Panel Quiz
Ever fancied pitting your wits against your colleagues? Demonstrate your knowledge and expertise in DNSSEC in our Great DNSSEC Panel Quiz. We are looking for four or five people to join us in a light-hearted quiz.
In addition, we welcome suggestions for additional topics. If you are interested in participating, please send a brief (1-2 sentence) description of your proposed presentation. Here are the relevant deadlines:
10 May 2012 — Deadline to submit brief description of presentation from interested participants
04 June 2012 — Deadline to submit presentation slides
Please respond to [email protected] no later than 10 May 2012 as indicated above. We hope that you can join us.
Thank you,
Julie Hedlund
On behalf of the DNSSEC Workshop Program Committee:
Luis Diego Espinoza, NIC .cr
Steve Crocker, Shinkuro
Simon McCalla, Director of IT, Nominet UK
Russ Mundy, Cobham
Ondřej Surý, NIC.cz
Lance Wolak, Vice President, Marketing & Sales, .ORG, The Public Interest Registry





Recent Comments