Upcoming workshops continue DNSSEC learning opportunities
Posted by Denise Graveline in Uncategorized on October 5, 2011
October and November bring more learning opportunities about DNSSEC, including these sessions:
- LACNIC, the Latin American and Caribbean Internet Addresses Registry, convenes LACNICXVI October 3-7 in Buenos Aires, with a DNSSEC tutorial earlier this week on October 3. NLNet Labs’ Olaf Kolkman, the workshop leader, has announced his goal that 2/3 of the workshop attendees turn on DNSSEC validation, and 1/3 sign their zone.
- The Internet Society’s Internet On conference in Buenos Aires October 5 includes a session on a new ISOC initiative to “create and promote resources that are easy to understand and quickly actionable by the very IT professionals responsible for the implementation of new technologies like IPv6 and DNSSEC.”
- Portugal’s .PT is sponsoring a cycle of fall workshops, including two on October 19 and November 18. The workshops are designed for professionals in the banking, public administration and judicial sectors.
- ICANN 42, taking place October 23-28 in Dakar, Senegal, is expected to include DNSSEC workshops; the workshop schedule has not yet been released.
Cisco whitepaper describes DNSSEC best practices for network implementation
Posted by Denise Graveline in Uncategorized on October 4, 2011
A white paper issued by Cisco, “Preparing for DNSSEC: Best Practices, Recommendations, and Tips for Successful Implementation,” reviews best practices for implementing DNSSEC in a network infrastructure and includes configurations for Cisco software, platforms and devices. The step-by-step instructions, aimed at Cisco-using network administrators, also include insights from internal testing performed by Cisco Security Research & Operations, such as how different versions of Cisco products will affect validation. Authors John Stuppi and Joseph Karpenko are members of the Applied Intelligence team in Cisco’s Security Research & Operations organization.
DNSSEC “gets more useful” in Windows 8
Posted by Denise Graveline in Uncategorized on October 3, 2011
Mark Minasi’s Windows Networking Tech page reports on what he learned at Microsoft’s recent BUILD conference about Windows Server 8. He notes that DNSSEC “gets more useful” in this version:
….DNSSEC is an up-and-coming technology that many of you will want to implement on your networks, and you also know that while Microsoft implemented DNSSEC in Windows Server 2008 R2 and Windows 7, their implementation was a bit uneven. You must sign your zone by taking it offline and running a few pretty long, ugly DNSCMD commands. It can’t validate zones that use the March 2008 RFC that introduces NSEC3, an inn0vation that most important zones are using.
With W8S, that changes. Its new DNS does NSEC3 and can be configured to automatically sign your zones as they change. Haven’t had time to try it out but it sounds pretty good.
Blog urges email admins to look beyond websites, use DNSSEC to secure email certificates
Posted by Denise Graveline in Uncategorized on September 30, 2011
The Email Admin blog urged organizations to consider DNSSEC as a solution to some of the most pressing email problems, from span and phishing to creating private emails. In this post, it noted how email administrators could benefit from widespread deployment of DNSSEC:
What’s good about DNSSEC is that it can be used beyond just authenticating website traffic. That Internet-wide authentication database created by the technology could also be used to authenticate email certificates. Those certificates would go a long way in reducing spam, muzzling phishing attacks and enabling private email—email that’s encrypted and can only be decrypted by its intended recipient. In order for that to happen, however, DNSSEC needs to be adopted throughout the cyberspace food chain—from those at the top of the domain structure to the ISPs to the browser and client makers.
DNSSEC certificates stable in Chrome
Posted by Denise Graveline in Uncategorized on September 19, 2011
Google’s Adam Langley reports on his Imperial Violet blog that all Chrome users now have DNSSEC-authenticated HTTPS in Chrome now that Chrome 14 is stable. The experimental feature “allows sites to use DNSSEC, rather than traditional, certificates and is aimed at sites which currently use no HTTPS, or self-signed certificates.” He also has documented the serialisation format.
U.S. Department of Defense clears way to sign .mil with DNSSEC
Posted by Denise Graveline in Uncategorized on September 8, 2011
The U.S. Department of Defense has authorized its Network Information Center to sign the .mil zone with DNSSEC, it was announced. The move is a major step forward in the U.S. government’s efforts to deploy DNSSEC across its domains.
Limited to use by the U.S. military, the .mil top-level domain will be signed over a three-month period, starting with an unvalidatable key and progressing to publication of the .mil key to allow validation across the Internet. The tentative timeline calls for the zone to be signed by December 12, 2011.
The .mil is a sponsored TLD and was one of the first top-level domains, created in January 1985. The U.S. is the only country with a top-level domain for its military.
Iran Gmail ‘man-in-the-middle’ attack prompts DNSSEC discussion
Posted by Denise Graveline in Uncategorized on September 2, 2011
A man-in-the-middle attach targeting Iranian users of Gmail left them vulnerable to having their logins stolen, and prompted discussion of DNSSEC’s security protocols. In “Google Users in Iran Targeted in SSL Spoof,” CNet News notes that DNSSEC offers an alternative to validating legitimate sites. From the article:
“The SSL ‘race to the bottom’ CA model is broken. Fraudulent certificates have been issued before, even without breaching a CA’s systems,” Johannes B. Ullrich, dean of research at the SANS Technology Institute, wrote in a blog post today. “But what can you do to replace or re-enforce SSL?”
DNSSEC (Domain Name System Security) can provide another way to validate that a site is legitimate, but it is not perfect, either, he said. In addition, there are browser plug-ins that implement reputation systems. One plug-in that has gained traction is Convergence, which works with Firefox and compares the certificate with other certificates received from the same site, he said.
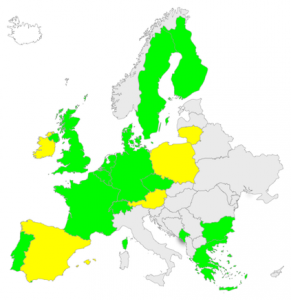
RIPE NCC posts maps of global DNSSEC deployment
Posted by Denise Graveline in Uncategorized on August 31, 2011
RIPE NCC–which has been signing its own zones since 2005–this week released updated global maps showing the progress of DNSSEC deployment. The report noted: “When the root zone has been signed in June 2010, this acted as a catalyst for TLD operators to deploy DNSSEC on their side. We have seen a gradual but significant increase in signed TLDs since then.”
The RIPE map of country code top-level domain DNSSEC deployment in Europe–one of several in the post–is shown below. Green indicates ccTLDs that have deployed to date; yellow indicates those with plans to deploy.
Slides now available for FOSE 2011 DNSSEC session
Posted by Denise Graveline in Uncategorized on August 15, 2011
Slides are now available for most of the presentations from the FOSE 2011 day-long session, The deployment diaries: DNSSEC in U.S. federal systems and beyond. Featuring a wide range of speakers from U.S. federal agencies and private-sector companies and nonprofits, the session looked at the progress toward U.S. government deployment of DNSSEC in the .gov domain, as well as deployment lessons from domains including .com, .net, .us, .uk and more. Presentations also included insights on validation, updates on DNSSEC and FISMA, advice on what to ask vendors and features of DNSSEC hardware and software solutions.
White House, senior Federal officials to speak on DNSSEC at FOSE
Posted by Denise Graveline in Uncategorized on July 14, 2011
A special workshop, “The deployment diaries: DNSSEC in U.S. Federal Systems and Beyond” will be featured at the FOSE conference and exposition on Wednesday, July 20, 2011. Several senior White House and federal officials are among the speakers who will address the workshop, including:
- W. Douglas Maughan, Cyber Security Division Director, Science and Technology Directorate, U.S. Department of Homeland Security
- Andy Ozment, Director for Federal Information Security Policy, White House National Security Council
- Doug Montgomer, National Institute of Standards and Technology
- Lee Ellis, General Services Administration
- Earl Crane, Department of Homeland Security
- Sean Donelon, Department of Homeland Security
- Scott Rose, National Institute of Standards and Technology
Joining the federal officials will be executives from companies, registrars and nonprofit providers of DNSSEC services and products, to discuss hands-on experiences with deployment, next steps such as validation, and available resources for federal IT managers working to meet OMB and FISMA requirements for including DNSSEC as an important part of cybersecurity protections.
In 2011, more than half of U.S. federal agencies have not yet deployed the domain name system security extensions (DNSSEC) mandated by OMB and FISMA. In the meantime, private-sector and international deployment continues in other domains around the world. This session will assess progress, identify lessons learned and offer new solutions and models for successful deployment, with an emphasis on solutions.
Participants will learn:
- Where their agencies stand compared to the rest of the .gov domain
- How DNSSEC fits into current cybersecurity priorities for the U.S. government
- Successful deployment models in the public and private sectors, from other domains, ISPs, registrars and more
- New apps, APIs, tools and products to help with federal deployment
The workshop includes break refreshments and requires an additional $35 fee over regular FOSE registration. You can register here.


Recent Comments